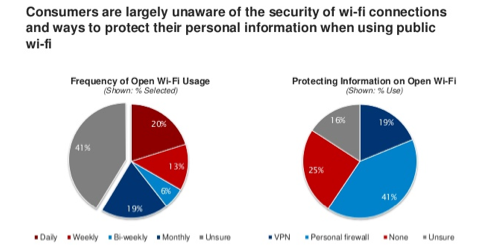
NEW YORK, NY – (February 25, 2019) - Private Communications Corporation (PCC), the leading provider of Internet security and mobile optimization utilities for consumers, today has officially launched its Video Optimization service. PCC’s Video Optimization technology dramatically reduces the data consumed when users are watching videos on YouTube, Instagram, Facebook, as well as over 40% [ Read More → ]

The internet of things—or IOT, as it’s commonly known—was once the stuff of science fiction, a newfangled “wave of the future” concept only experienced at futuristic demonstrations like the World’s Fair. But now many of these devices are already in use in millions of households around the world. They’ve become an interesting yet somehow still unknown entity in the world of technology, and industry experts have stated these products will be the norm just a handful of years from now.